We do actual pentests – not just scans.
Vulnerabilities Die Here.
Cyber threats don’t wait. Neither should you. At ScriptJacker, we go beyond automated scans, performing deep manual penetration testing to identify and eliminate real-world vulnerabilities before attackers do.
- One Client at a Time – 100% Focus
- Quality Over Quantity – No Rushed Reports
- Web, API, Mobile & Network Security Testing
Services we provide
At Scriptjacker, we go deeper than automated scans. We uncover hidden vulnerabilities across your web, API, mobile, and network systems. With flexible engagement models—project, contract, retainer, or subscription—we provide tailored, actionable insights that transform your security posture. Discover real protection, Where vulnerabilities die, and security thrives.
Web Application Pentesting
We simulate real-world attacks on your websites to uncover hidden vulnerabilities, ensuring your online presence remains robust and secure.
API Security Testing
Our experts rigorously test your APIs to safeguard data integrity and prevent unauthorized access, keeping your integrations bulletproof.
Mobile Application Security
We evaluate your mobile apps for vulnerabilities and compliance issues, ensuring a secure and seamless user experience.
Network Pentesting
We simulate real-world attacks on your network to identify vulnerabilities in firewalls, routers, and internal systems. Our actionable recommendations help you strengthen defenses against unauthorized access.
Phishing Simulation
We conduct controlled phishing tests to evaluate your team’s ability to spot suspicious emails. The results guide targeted training, reducing the risk of successful phishing attacks.
Custom Needs
Have unique needs? We tailor our security services to fit your specific requirements. By combining elements from our standard offerings, we craft a personalized strategy that addresses your exact challenges
Our Engagement Models
we understand that every business has different security needs. That’s why we offer flexible engagement models tailored to your requirements. Whether you need a one-time assessment or ongoing protection, we provide the right approach to keep your digital assets secure.
Project-Based
You are having lots of projects? We’ll assess your web apps, APIs, mobile apps, or network for vulnerabilities, provide a detailed report, and guide you on fixing the issues. Best for businesses that want to test specific assets before launching or after major updates.
Contract-Based
Want long-term security? We provide scheduled pentests and continuous security evaluation over a fixed period. Ideal for businesses that need security as part of their long-term strategy.
Retainer Model
Need ongoing security support? We act as your security partner, performing regular vulnerability assessments, quick response to threats, and on-demand testing whenever required. Perfect for businesses looking for continuous protection.
Subscription-Based
Prefer predictable costs with ongoing security? We offer frequent security assessments, vulnerability management, and compliance checks at a fixed price. A great choice for businesses that want regular security coverage without surprises.
Custom Model
Have specific security needs? Tell us what works best for you. Whether you need a combination of models or something unique, we’ll tailor our services to fit your business requirements.
Our Approach
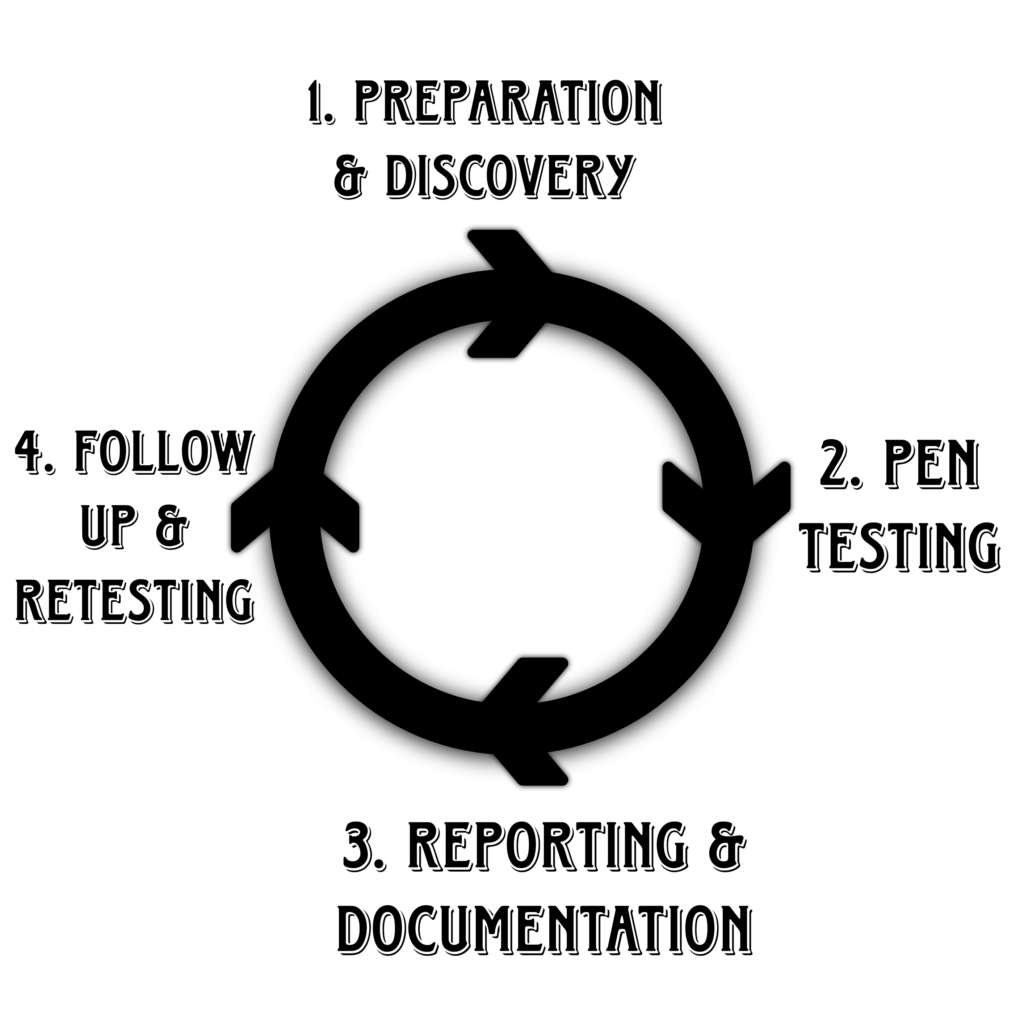
01.
Preparation & Discovery
Before starting, we talk with you to understand your business and identify the key systems that need protection. We gather all the necessary details so we know exactly where to focus our efforts. This step ensures that our testing is targeted and effective.
02.
Penetration Testing
With a clear plan in place, we begin our testing. We simulate real cyberattacks to check for any weak spots in your web applications, APIs, mobile apps, and networks. Our aim is to find any vulnerabilities that could be exploited, giving you a true picture of your security.
03.
Reporting & Documentation
After testing, we prepare an easy-to-understand report that lays out everything we found. The report explains each issue in simple & professional way and offers practical advice on how to fix them. This way, even non-technical team members can understand the risks and the steps needed to address them.
04.
Follow Up & Retesting
Once you’ve made the changes, we return to verify that the fixes work as expected. We also discuss the findings, answer questions, and suggest any further improvements. This follow-up ensures that your systems stay secure over time.
What You Get?
After our assessment, we provide a comprehensive results package that tells you exactly what we found and what steps to take next. Here’s what you can expect:
Delivered in the format you prefer—PDF, DOC, email, or any other format that works best for you.
A meeting to review the results, address your questions, and confirm that the applied fixes are effective.
A concise overview of your overall security posture, perfect for non-technical decision-makers.
Every issue is broken down in detail. You’ll get a full description of each vulnerability, along with clear steps to reproduce it, an assessment of its impact, explanation of how it might be exploited, a severity rating, and actionable recommendations for remediation.
A polished final report crafted to meet industry standards, ideal for compliance and record-keeping.
A custom-prepared report reflecting our hands-on testing and expert insights, ensuring you get a true picture of your security.
Who We’ve Secured
Big or small, local or global—our security covers every business.
Accurate Reports & Constructive Discussions

ScriptJacker Delivers Reliable Security

Crafting Security, Creating Trust
Ever wonder if your current security measures are really enough? Discover how ScriptJacker’s hands-on, personalized approach uncovers every hidden vulnerability to keep your business truly safe.
Personalized Attention

At ScriptJacker, we take a focused approach—one client at a time. This ensures that every test is detailed, every report is precise, and every security recommendation is crafted for your unique environment.
Flexible Engagement Models
Security needs differ for every business, and so should the approach. Whether it’s a one-time security assessment, project-based testing, or ongoing security monitoring, we offer custom engagement models that align with your goals.
Real-World Manual Testing

We go beyond automated scans—manually simulating real-world attacks to find vulnerabilities that standard tools miss. This means you get a comprehensive and practical security evaluation, ensuring your defenses hold up against actual threats.
Detailed & Actionable Reporting

A vulnerability report should do more than list issues—it should help fix them. Our reports provide clear, step-by-step with risk prioritization, so your team can resolve security gaps effectively and efficiently.
Follow-Up & Retesting

Security isn’t a one-time task. After remediation, we conduct retesting to verify that vulnerabilities are fully resolved, ensuring that your security remains strong and nothing is left unprotected.
Cost-Effective Solutions

Security should be accessible without compromising quality. Our pricing adapts to your business size, scope, and security needs—delivering high-value assessments while staying budget-friendly.
Rapid Response

Time is critical in cybersecurity. Whether it’s starting an assessment, delivering reports, or providing support, we ensure quick turnarounds to keep your business secure without unnecessary delays.
Quality Over Quantity

Every vulnerability we report is validated and meaningful. Instead of overwhelming you with unnecessary details, we focus on high-quality insights that truly strengthen your security posture.
Is Your Business Secure Enough?
Security isn’t a one-time task. When was the last time you tested yours? From in-depth pentests to ongoing security partnerships, we help you stay ahead of threats. Let’s discuss your needs today!
























